Understanding CSRF Attacks
While OAuth offers a powerful framework for secure authorization across various services, it is not infallible from vulnerabilities. Login CSRF attacks are one instance of vulnerabilities that may arise when using OAuth, and the nonce technique functions as an effective tool to defend against potential breaches.
Introduction
For application developers, having a comprehensive understanding of security vulnerabilities and proactive measures used to protect their systems is essential. This post explores the specifics of login CSRF attacks, providing insight into their mechanics as well as demonstrating how nonce, an acronym for "number used once" to describe a unique random string, can be used to safeguard your application’s security.
What Is a CSRF Attack?
A Cross-Site Request Forgery (CSRF) attack is a type of security vulnerability that tricks a user into unwittingly performing actions on a web application to which they are authenticated. Unlike other types of attacks, CSRF exploits the trust that a website has in the user’s browser, circumventing the need to target the user.
Practical Example: Login CSRF
During a login CSRF attack, an attacker deceives a user into unknowingly logging into the attacker’s account, often with the intent to collect private information from users who mistakenly believe they’re accessing their own account.
An attack scenario might look like this:
- The Attacker sends a crafted link or embeds a malicious request, aiming to trick the User into clicking or loading it.
- The User clicks on the link or loads the malicious content, often unknowingly initiating a login request to the application, but with credentials or context for the Attacker's account.
- The application processes the request, thinking the User wants to login to the Attacker's account.
- The User is logged into the Attacker's account on the application.
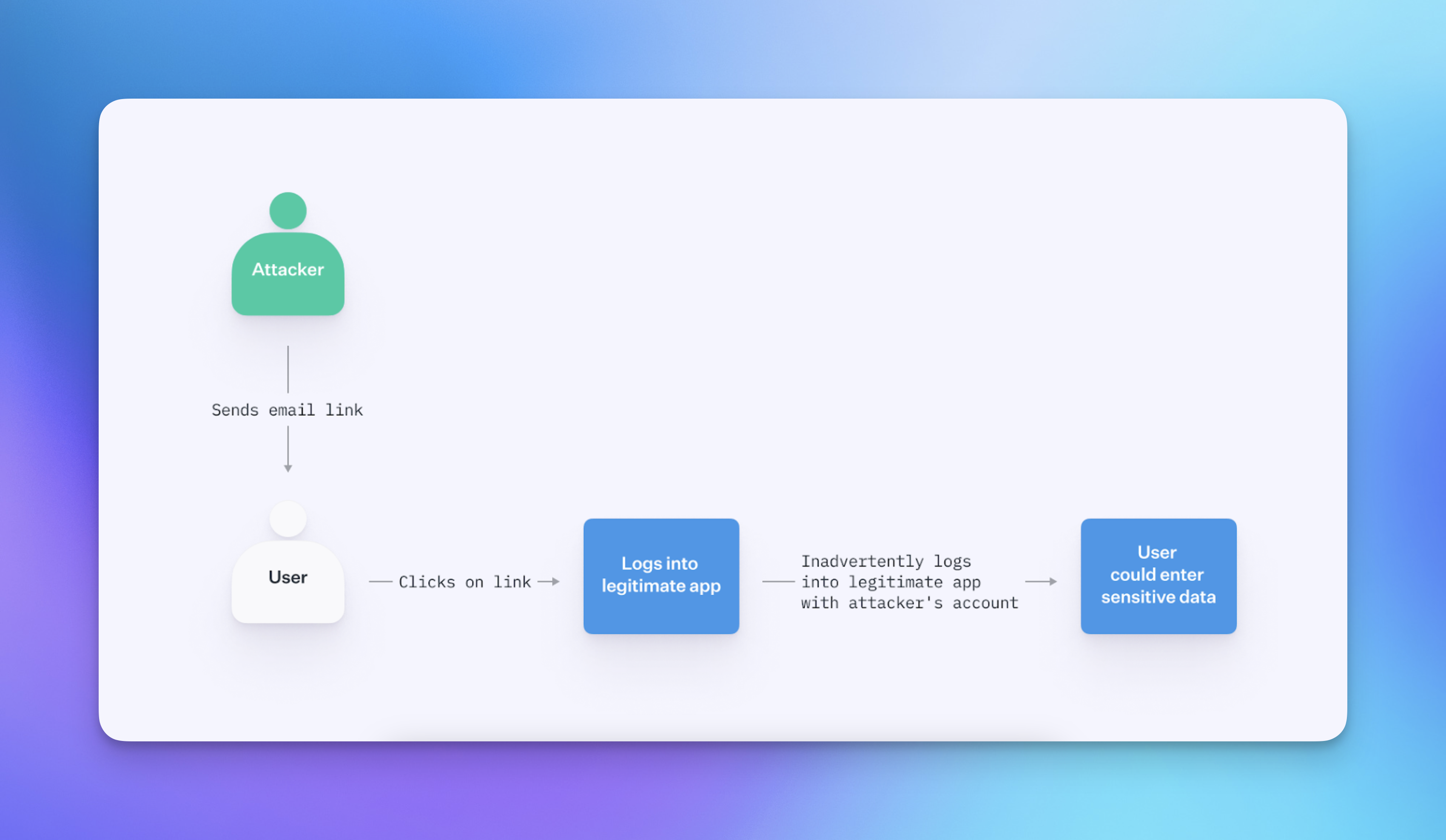
Login CSRF attacks are generally considered less severe than other types of attacks, because many users will recognize that they’re logged into the wrong account. However, the consequences of a successful attack can still be significant, since users may not realize the mistake until it’s too late.
Preventing Login CSRF Attacks: the Nonce Technique
Enter the 'nonce' technique—a method that has gained traction for its efficacy in mitigating the risk of CSRF attacks during OAuth flows. A nonce is a unique, random string that is generated for each OAuth process. It functions as a CSRF token, securely validating that the client application making the request is the one to which the server responds. This process involves generating a nonce, hashing it for secure storage, and validating it server-side to ensure the integrity of the OAuth flow.
Here's how you might use this technique:
- Generate a random value (nonce): Use your server-side language of choice to generate a secure random value, also known as a nonce. This value will be used later to prevent CSRF attacks. In this example we’ll use Node’s built-in crypto library:
- Store the hashed value: After generating the nonce, hash it and store it in a short-lived session cookie within the user's browser.
- Pass the nonce in the state parameter: During the OAuth authorization process, send the nonce as a state parameter to the OAuth authorization server. Here, the original nonce (not the hashed one) should be included in the state parameter when redirecting the user.
With WorkOS:
- Server-side validation: Upon the user's return to your application, validate the nonce to ensure it is legitimate and thus prevent CSRF attacks. The nonce received in the state parameter is hashed and compared to the hashed nonce stored in the session cookie.
With WorkOS:
Conclusion
OAuth offers a powerful framework for secure and smooth authorization across various services, but it is not infallible from vulnerabilities. It is crucial for developers to fully grasp these potential risks to effectively prevent unauthorized access and other malicious activities.
The nonce is an effective tool for mitigating vulnerabilities that may arise from OAuth flows. In addition to defensive mechanisms like the nonce, continuous updates, user education, and persistent monitoring can strengthen your application’s security from potential breaches.